CHEAT SHEET
- As goes California. The California Consumer Privacy Act (CCPA) served as a model for 15 other US states to construct their own privacy legislation.
- Privacy maturity. One way to assess your organization’s privacy capability is to measure your current and desired target on a scale of preparedness, with one being “immature” and five being “enabling.”
- National guidelines. All 50 US states contain data security breach notification laws with penalties. Organizations would be wise to review and strengthen their programs in conjunction with the state laws.
- Third parties. Companies must have the capacity to address personal information they gather that is either sold or shared with third parties. This can be done with appropriate service level agreements outlining data handling expectations and restrictions.
Are you ready? Led by California, a new wave of privacy legislation is likely to have significantly more impact and cause more difficulty for organizations than any other US compliance requirements seen within the past decade. These new rules will create new obligations and privacy challenges for organizations. Companies will need to rethink the concept of Personally Identifiable Information (PII) and implement new policies, processes, and technology to develop a dedicated privacy plan. For organizations subject to these requirements, the key to avoiding substantial risks and costs associated with these new requirements is by being properly prepared. This article details key strategies and capabilities organizations should be prepared to implement to meet emerging privacy requirements.
On June 28, 2018, the California Legislature passed the California Consumer Privacy Act (CCPA). Similar to the data breach legislation initially passed in California in 2003 that served both as a model and was a catalyst for multiple states adopting similar laws, the 2018 CCPA is also expected to be copied by many other states and even perhaps spur the passage of federal privacy legislation. Recently both Nevada and Maine also passed somewhat less restrictive privacy laws. While the CCPA is expected to go into effect on January 1, 2020, in what appears to be a wave of new legislation at the time of publication, at least 15 other states are considering or have proposed their own privacy legislation.
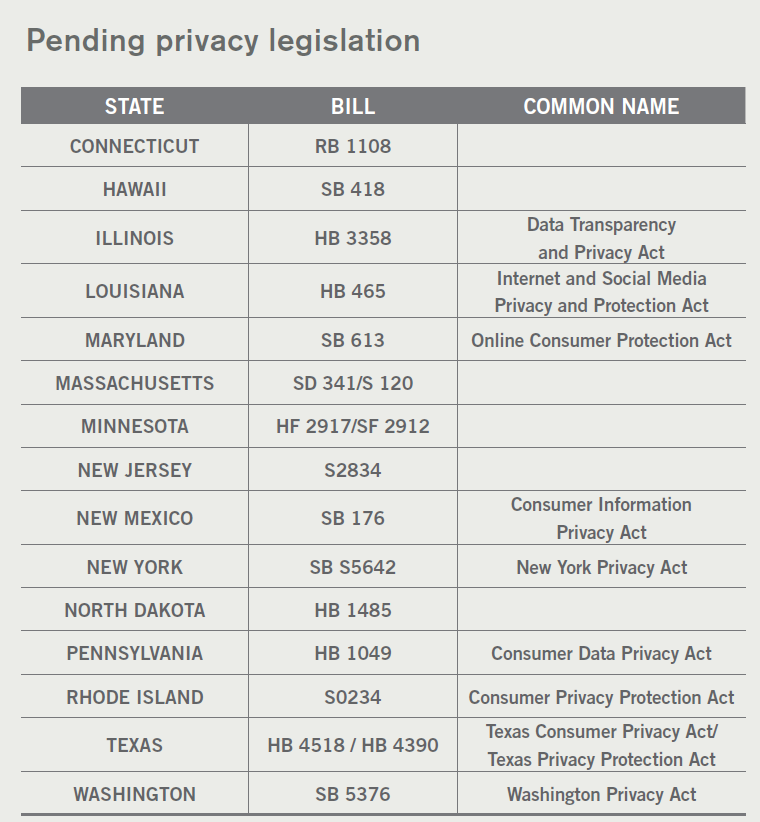
In general, these new and proposed state privacy laws are designed to provide consumers a broad set of rights over the use and retention of their personal information. The CCPA gives consumers broad rights to access and control their personal information and imposes technical, notice, and financial obligations on affected businesses. In addition, it will expand the definition of personal information to include types of data not traditionally considered personal information in the United States. Under the CCPA, personal information encompasses any information that could be reasonably linked, directly or indirectly, with a particular California consumer or household.
The CCPA is designed to provide consumers and eligible employees with five explicit rights. These include the right to opt-out of the sale of personal information (or opt-in for consumers under the age of 16), right to access, right to deletion, right to portability, and the right to nondiscrimination.
As more states adopt their own privacy legislation, it is entirely possible that new requirements distinct from either the CCPA or the EU General Data Protection Regulation models will emerge. Perhaps most importantly, CCPA and other states’ laws will be enforced by both regulators and through a right of private action, potentially spurring significant lawsuits, from class action suits to one-off lawsuits.
Organizations subject to CCPA compliance requirements and other new privacy laws must address some difficult questions: How do we implement an enterprise-wide privacy program that meets the patchwork of individual state (and potentially federal) requirements? How do we implement a privacy program when many of the requirements are still being defined and modified? How do we build organizational literacy and compliance programming that accounts for ambiguity within the CCPA? What is defensible and sufficient for CCPA compliance? Are all levels of the organization ready to operationalize CCPA?
Instead of focusing on meeting each state’s requirements as they arise, the more strategic approach is to develop general privacy policies and personal information governance and handling processes. Once the organization has a solid program in place, it can make program adaptations as necessary to account for additional privacy requirements. There are generally enough similarities across all the various existing privacy regimes that organizations can build basic privacy capabilities around classification, information security, production, and disposition. These basic privacy capabilities — or what can be referred to as privacy information agility — should meet most or nearly all of the organization’s compliance needs across states. While the ability to adapt to the regulatory environment may be necessary. This approach will be far easier in the long run when compared to developing a privacy program hardwired for a single state, only to have to update the program continuously as states adopt new or additional privacy legislation.
Will there be a federal privacy law?
Shortly after California passed its privacy law, both privacy advocates and companies have been calling for a federal privacy law that would supersede a patchwork of state laws. Privacy advocates want to ensure that such a law would be as strict as the state laws it would be replacing. Likewise, companies see a federal law as one of their last chances to enact less restrictive requirements. Most privacy experts believe that the US federal government will pass such a law, but its timing at this point is uncertain.
Key characteristics of privacy information agility
Designing a privacy program to meet a single state’s privacy requirements may increase the risk of substandard compliance across the regulatory environment in which an organization operates. The organization will have to update and redesign their privacy program each time new privacy laws are enacted. The smarter approach is for organizations to consider building baseline privacy protocols that can be easily adapted for changing requirements. This baseline capability is called privacy information agility. Privacy information agility is characterized by these core capabilities:
Do you know what personal information you have and where it is? A key first step is knowing what type of personal information is collected, how personal data flows through the organization (both internally and externally), and where it resides. Consider a data mapping initiative to understand how personal data is processed within your organization.
How is the personal information managed and stored? Determine where the personal information resides and evaluate if it is in a secure environment.
Can you search for the personal information? Establish best practices and develop the process to efficiently search for and produce personal information from an individual consumer or employee.
Do you know where the personal information goes? Review vendor contracts and identify all parties with whom the personal information is shared.
Can you delete it? Evaluate your retention policies and determine whether or not you can you defensibly and easily delete this information upon request?
Many privacy requirements can be met through a focus on developing these core capabilities.
Eleven ways to assess your organization’s privacy capability
1. Target the right privacy maturity
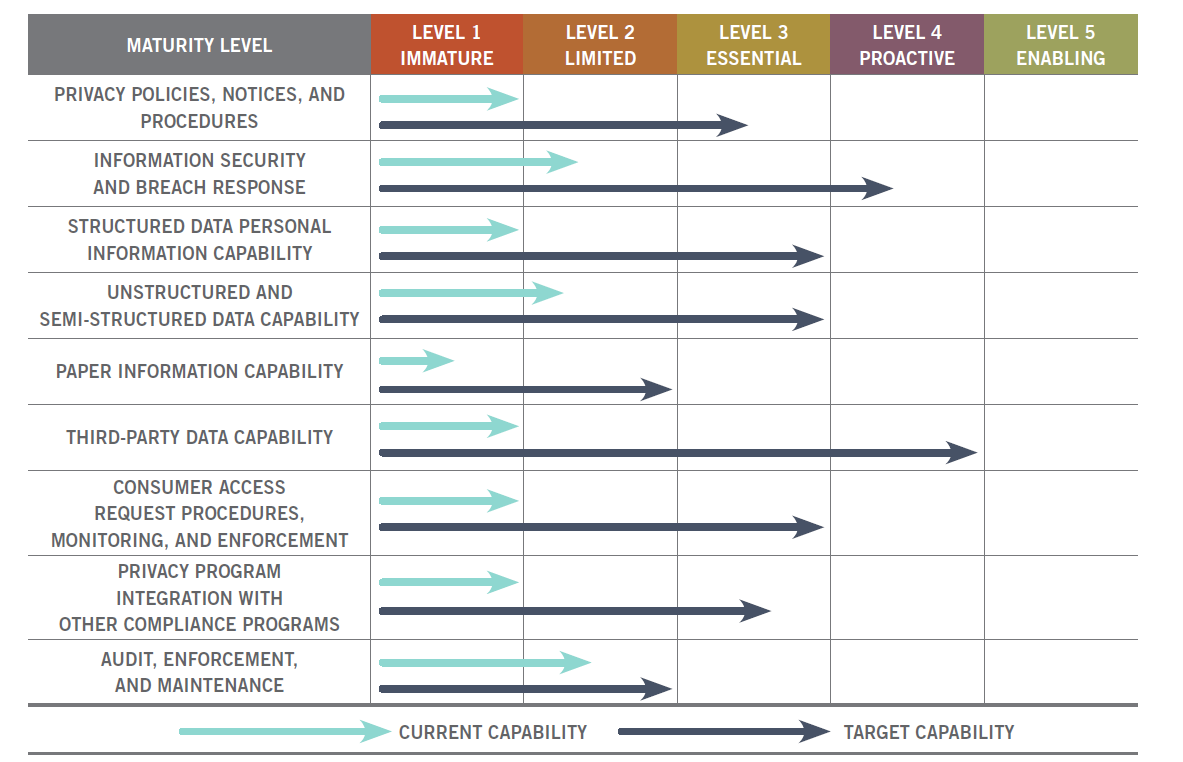
Privacy maturity is the concept of reviewing your current capabilities in various privacy areas against your desired target capability. The goal is to measure your current and desired target capability on a scale of preparedness, usually where level one is an “immature” rating all the way up to a level five rating of “enabling.” Savvy privacy professionals know that targeting the right level of privacy maturity is key. Each area in your privacy program may not need to be at the highest level to perform successfully, address vulnerabilities within existing processes, and comply with privacy laws. Utilizing a maturity capability model allows the organization to determine the best level of preparedness for their specific privacy concerns. Organizations should consciously target a specific maturity level and build their programs to meet that level. Figure 1 displays a maturity capability model showing current versus target privacy program capabilities.
Different levels of privacy program maturity are required for different organizations. Organizations vary on the number of consumers whose personal information they collect or process, what they do with that personal information, the quantity and breadth of this information, how widely it is shared, and how this information is stored and managed. A few organizations will indeed need a highly advanced and rather expensive “sports car” level of privacy program maturity; however, many organizations can be better off with a fully capable and more cost-effective “sedan” or even “golf cart” level of privacy program maturity. It is better to have a well-executed, albeit simpler, approach than a more complex, difficult, and expensive “sports car” target maturity that spends more time in the repair shop than being driven.
Organizations fail in their privacy efforts by overreaching and trying to create target capabilities that are too sophisticated or unmanageable for the long term.
2. Privacy policies, notices, and procedures
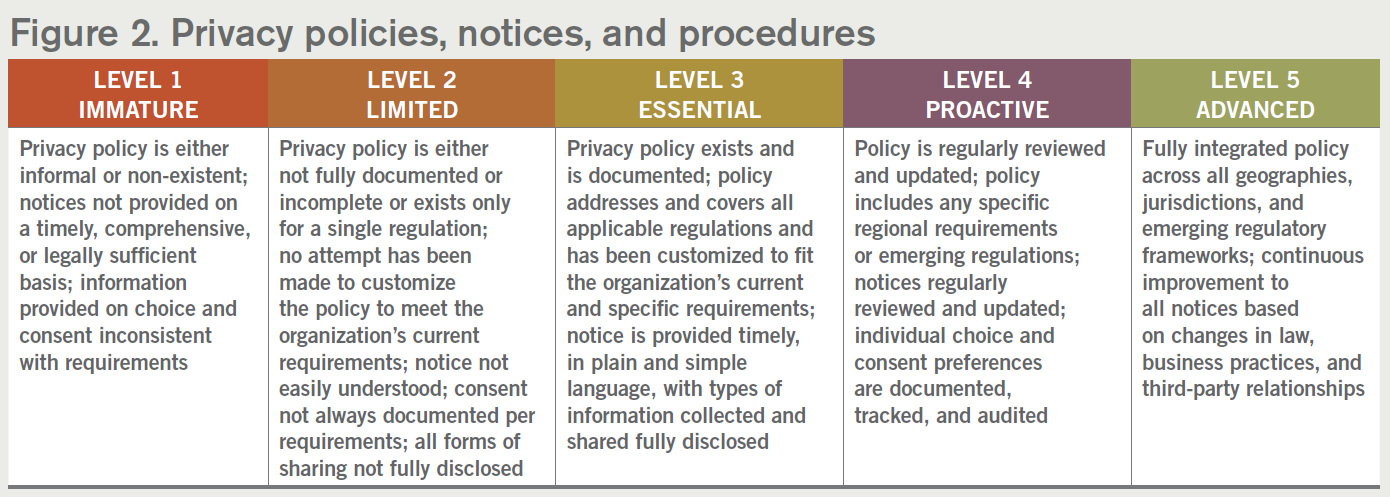
The CCPA will require affected organizations to either create a privacy policy or review and update their external privacy policy and notices. Organizations will also need to update and add notices, as well as create new processes and procedures.
Keep in mind that the development of the privacy policy is as important as the execution of the privacy policy. Many aspects of the CCPA, as well as other privacy legislation, are nonprescriptive, and a risk is that an organization will put significant effort into creating an extremely detailed privacy policy at the expense of its execution. The main thrust of the privacy program becomes simply having policies. To avoid this, it may benefit an organization to develop a solid privacy policy, and then dedicate resources to focus on ensuring they are executing and operationalizing that policy by classifying, securing, managing, and building the capabilities to comply with CCPA.
3. Privacy organization and awareness
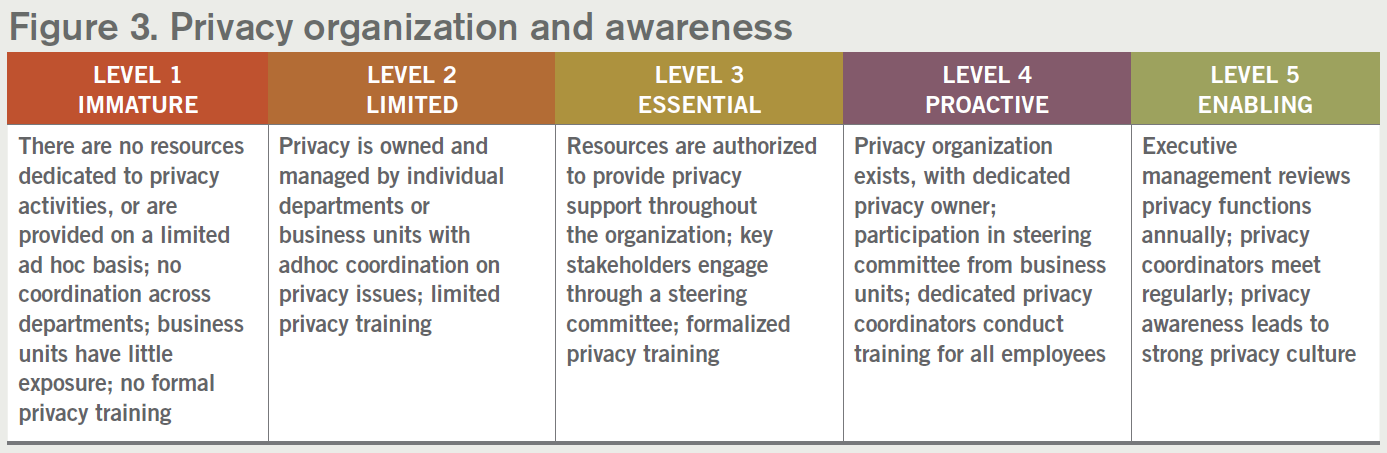
Depending on your organization, anticipate that compliance with CCPA and similar privacy regulations may be a culture shift on several levels. A single person serving as the organization’s privacy officer and updating a privacy policy once a year will not be sufficient. A well developed privacy program should not be viewed as a check-the-box operation — it is a living program with ongoing responsibilities throughout the organization. A successful privacy program must identify and engage stakeholders from throughout the organization. It should not be seen as something that only the legal department takes on or only the IT department implements. It often includes organizing a cross-functional privacy steering committee, creating and conducting privacy awareness training, and building executive-level support. Compliance with the new privacy regulations such as CCPA will not be a one and done matter. You will need to implement a long-term plan. Your organization is constantly changing — and your privacy program must follow suit.
4. Information security and breach response
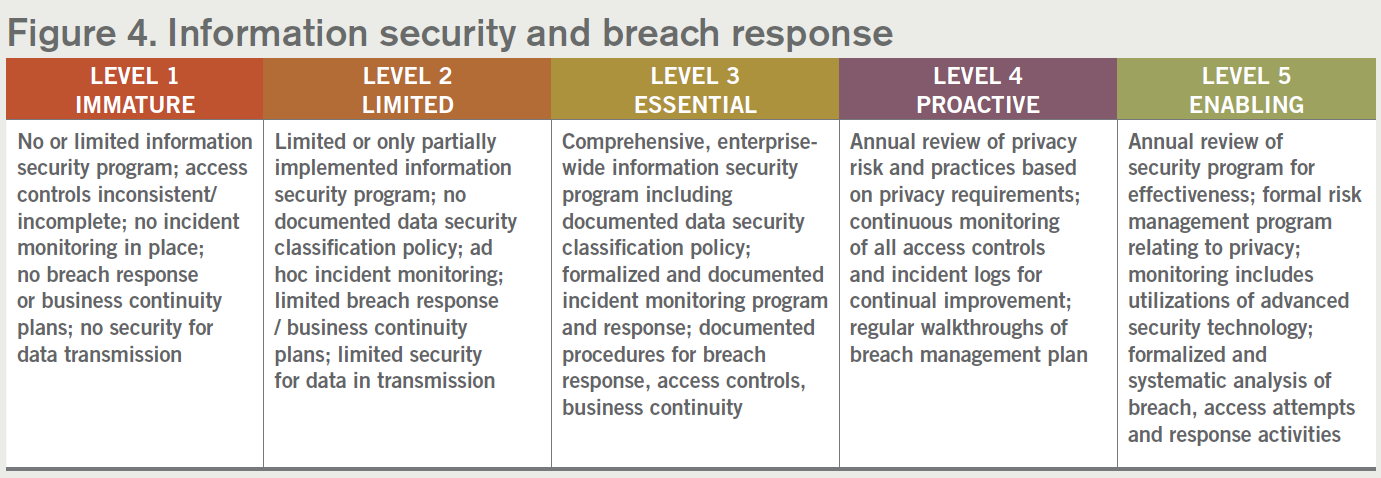
The CCPA and similar privacy laws have strong penalties and enforcement measures for organizations in the event of a data breach. There are already existing data security breach notification laws with penalties on the books in all 50 states. With the enforcement measures and penalties prescribed under new privacy laws, organizations should review and strengthen their data security programs, including their breach response policies and procedures. It will also be important to review the data security practices of third parties and service providers that you provide, sell, or share personal information with. Most organizations have some level of information security program already in place. The exact security program your organization needs will depend on the type, medium, and location of the personal information.
5. Structured data capability
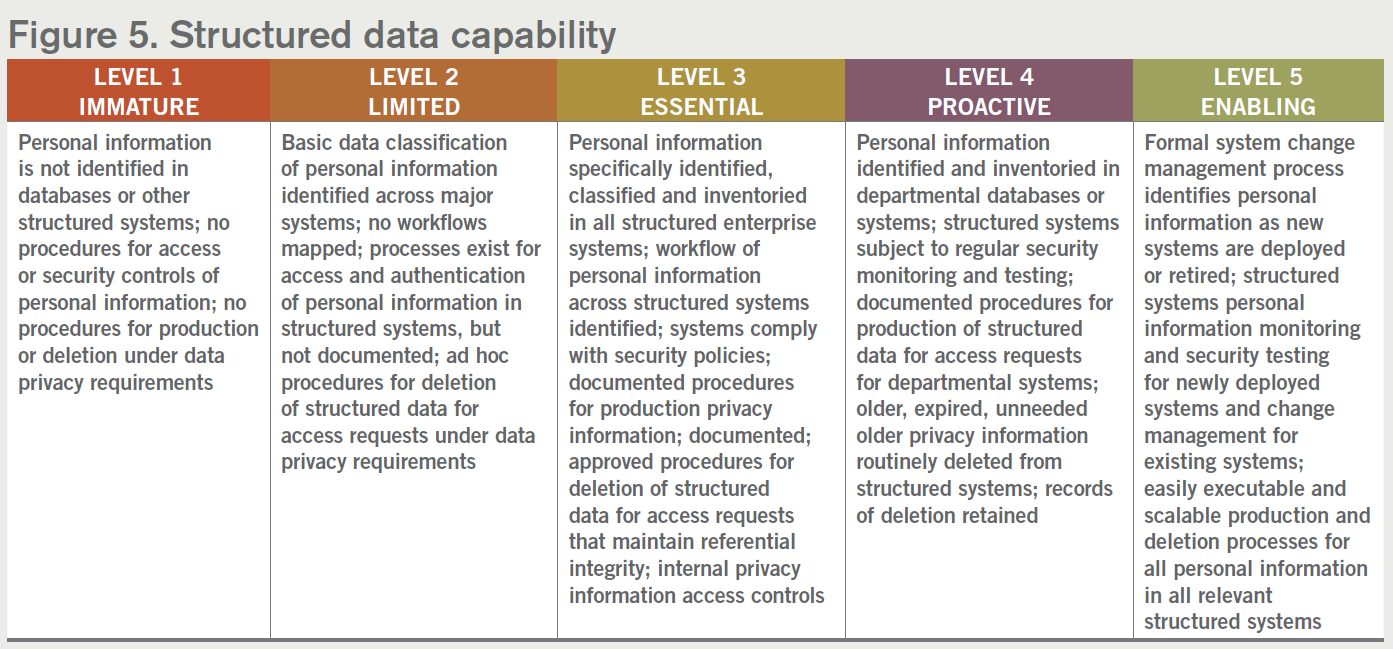
Significant amounts of personal information may live in applications that store that information in structured databases. These databases are often homegrown applications within the organization or third-party applications that the organization has contracted to use. Personal information often flows from one system to another, sometimes creating many copies of the same data. Organizations need to develop capabilities for managing this structured personal information.
Privacy compliance requires the capability to identify and secure personal information in these structured databases, and also the capability to produce personal information in response to a consumer or employee access request, as well as deleting or “de-identifying” it through pseudonymization procedures.
6. Unstructured and semi-structured data capability
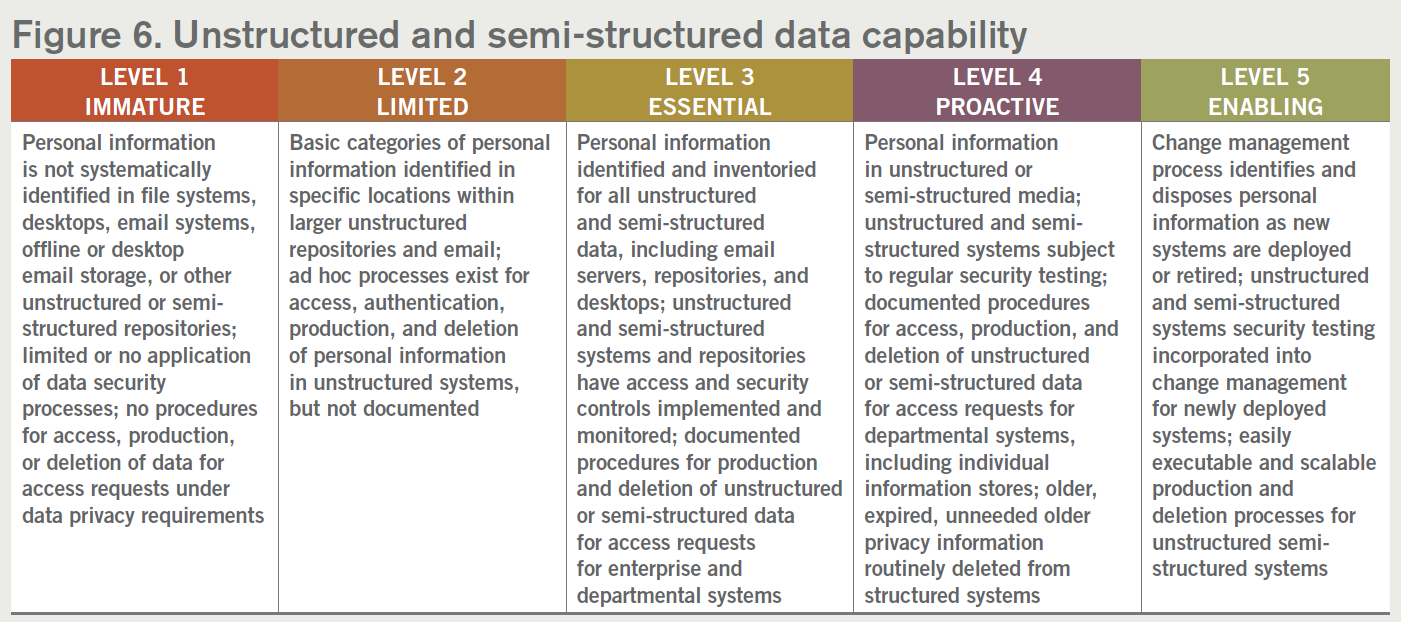
While personal information is typically associated with information in structured databases, large amounts of personal information may exist in unstructured and semi-structured formats. Examples of unstructured or semi-structured data can include shared file drives, email messages, word processing documents, videos, photos, audio files, and other kinds of common documents. Many organizations fail to address unstructured and semi-structured data, potentially creating risk for noncompliance issues. Under the CCPA and other privacy laws, personal information stored in unstructured or semi-structured formats or locations is in scope and can be particularly challenging to manage. Consider identifying sources of unstructured and semi-structured data and consider end user access controls and data handling best practices to account for the type of information stored in these locations and focus on employee training and improving visibility of these sources.
7. Paper information capability
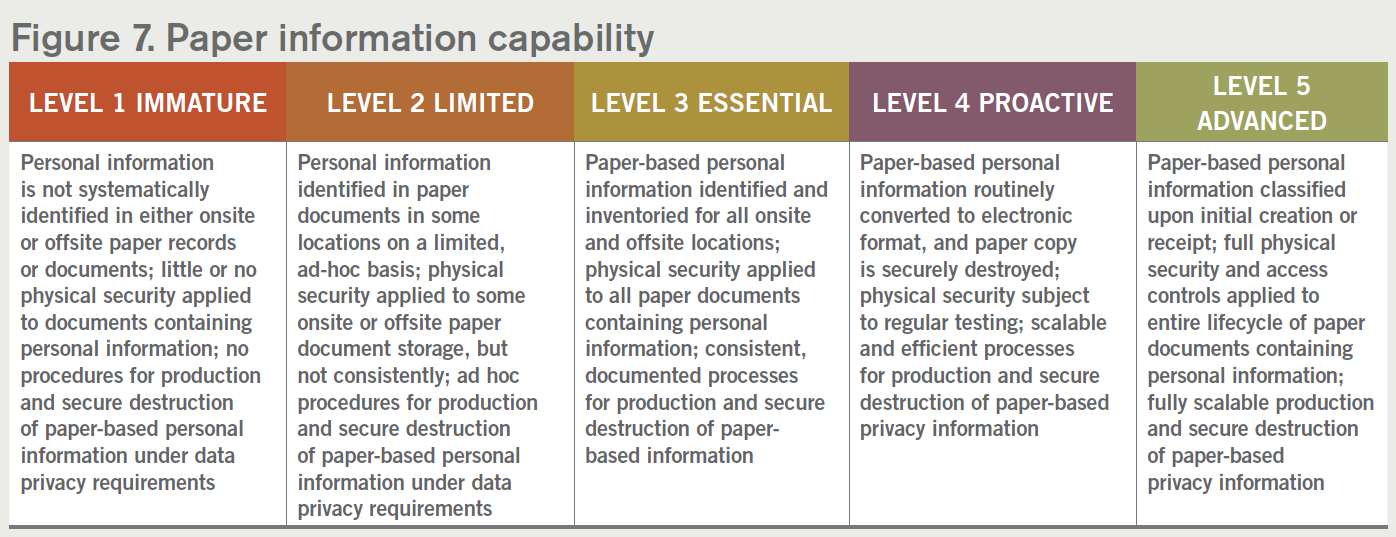
In most organizations, paper documents tend to accumulate in both onsite and offsite storage facilities, some of which will most likely contain a significant amount of personal information. CCPA and other new privacy laws do not exclude paper records, and as such identifying and producing this paper-based information can be particularly burdensome. Hence, an organizations privacy program must address paper documents and third-party storage.
Often paper-based personal information is either scanned into an electronic format or ideally destroyed as soon as its organization-prescribed retention period is reached.
8. Third-party data capability
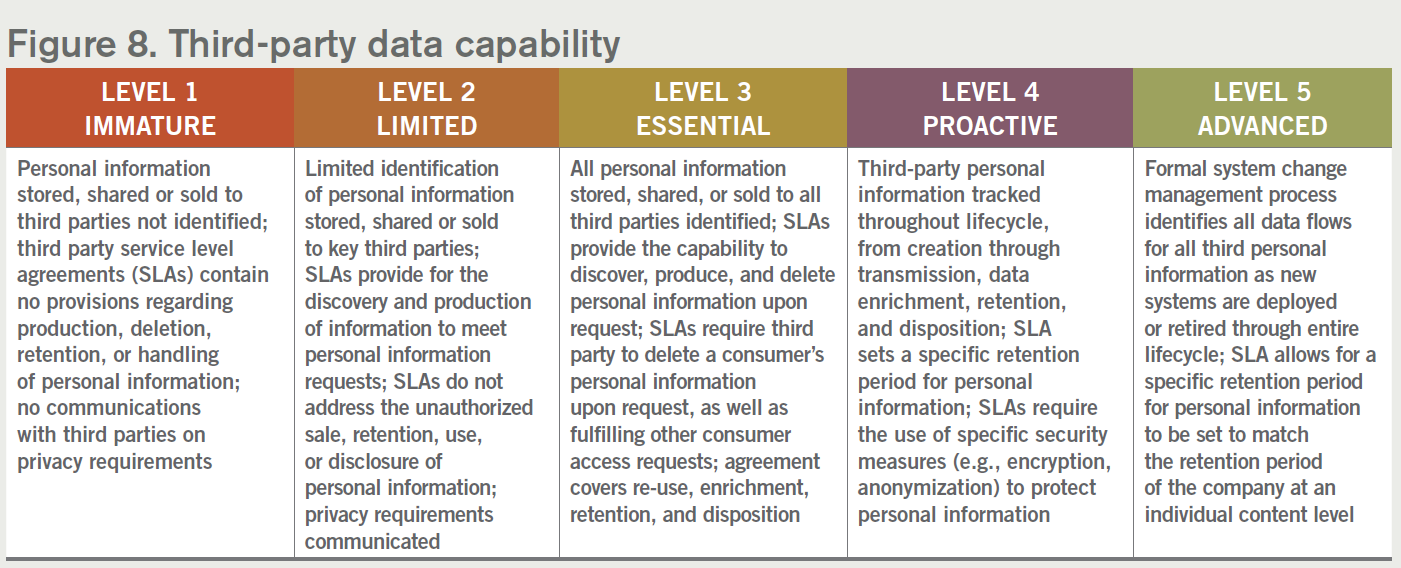
Organizations must have the capability to address the personal information they collect that is either sold or shared with third parties, or likewise that they receive themselves. This includes developing the appropriate Service Level Agreements (SLAs) that outline data handling expectations and restrictions as well as ensuring that all third-parties have the capability of complying with the privacy requirements. Many organizations are surprised to find out the extent to which personal information may be shared by third parties.
Well-designed third-party capabilities set clear expectations over who is responsible for what. This is always easier to address proactively. Developing clauses to promote data handling in compliance with privacy laws and obligations should help minimize misuse or lack of insight into how personal data is managed once it is shared externally.
9. Consumer access request procedures, monitoring, and enforcement
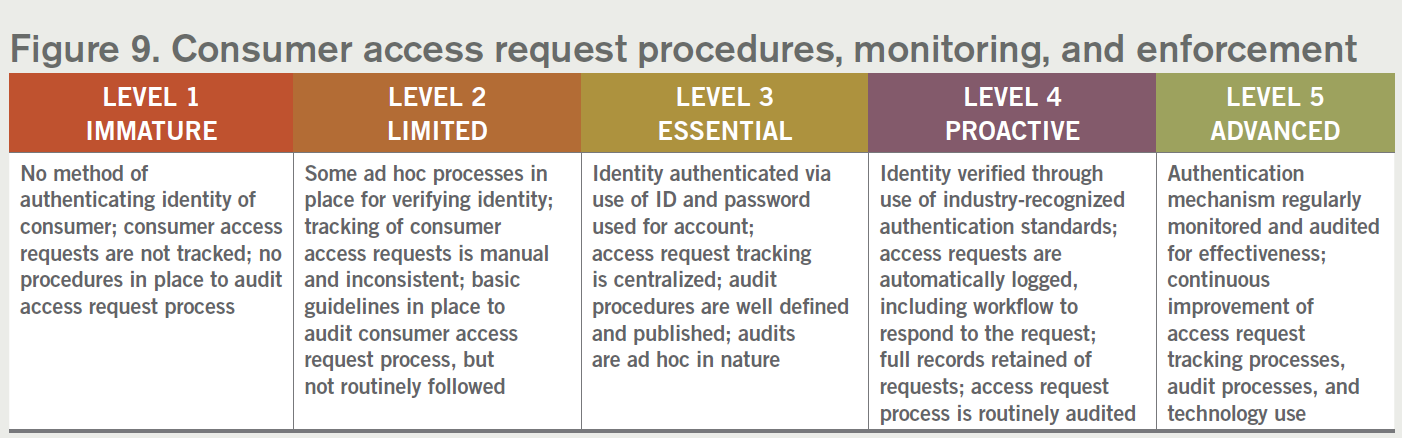
CCPA and other proposed laws require a series of processes to support consumer access, production, and deletion requests. These include authentication processes, search processes, production processes as well as deletion processes. Furthermore, these processes need to be tracked and monitored for compliance.
10. Integration with other compliance programs and processes

One of the problems that has emerged from the CCPA and similar privacy laws is the need for the privacy program to coordinate with other existing compliance regimes within the organization, including records management, compliance with other existing privacy laws (e.g., HIPAA, FERBA, GLBA), as well as eDiscovery and legal holds. The CCPA, for example, would not require requests for deletion of personal information under an organization’s legal hold, but these two groups of processes need to be coordinated.
11. Audit, enforcement, and maintenance
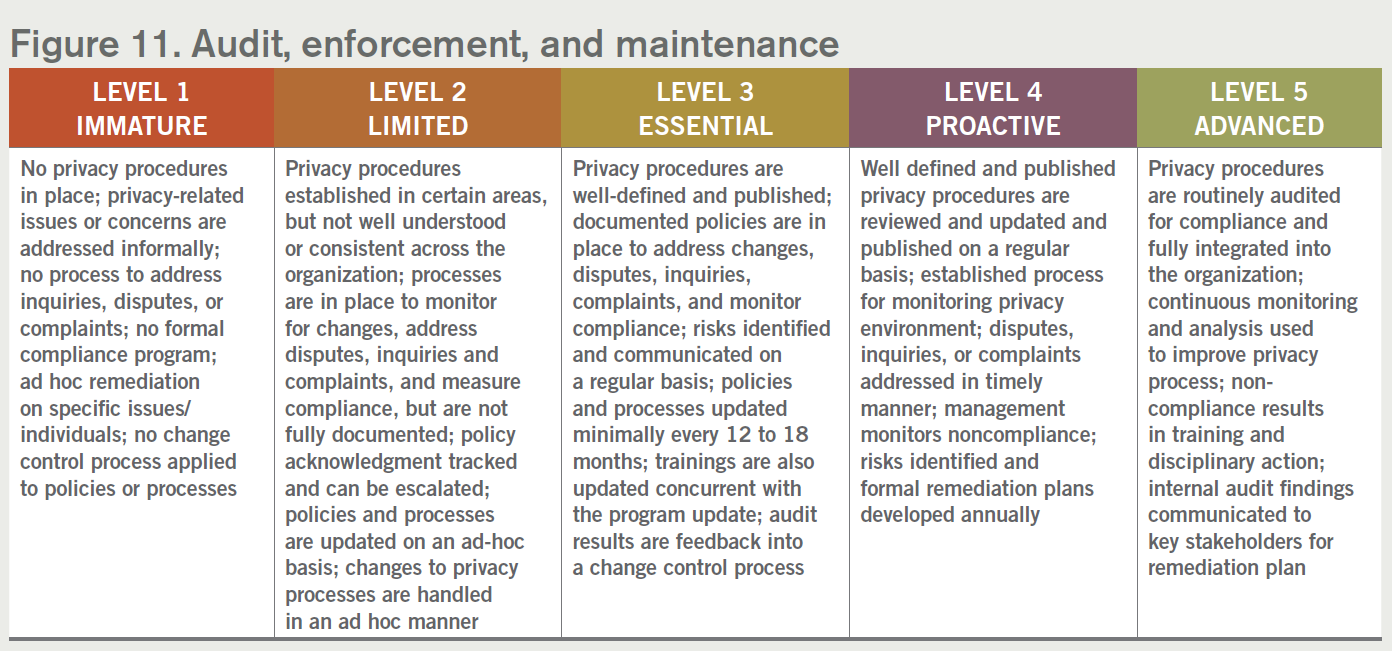
Finally, privacy laws and the resultant programs are hardly stagnant. New laws are being enacted and current legislation is subject to amendments as well as implementation guidelines. To this end, privacy programs should not be thought of as “one and done,” but rather have audit, enforcement, and maintenance processes built within them.
Final thoughts
New and emerging privacy requirements like the CCPA can be both daunting and overwhelming. With significant risks and penalties for noncompliance, it can be challenging to assess what level of privacy maturity is needed for any given organization’s privacy program. Organizations should avoid the desire to start looking for the perfect policy, the perfect process, or the perfect tools. Additionally, organizations should avoid the mentality that they are not ready to start the CCPA compliance process because they are not at 100 percent in their privacy program. In the meantime, documents and data accumulate, privacy requirements become stricter, and the risks increase. Perfect becomes the enemy of good.
You may be asking: How much is enough to comply with CCPA and other similar privacy laws? Privacy is an inherently imperfect process. Fortunately, the courts and regulators generally do not expect perfection. Rather, they expect reasonable, good faith efforts to comply. In your policies, declare what will be done. Execute those policies with processes, technology, and training. Demonstrate that policies are being complied with through training and audits. Show that a plan has been developed. Show that the plan is being executed. Audit the results and remediate any shortfalls. Not perfect? That is OK. Start with good and keep moving forward.
ACC EXTRAS ON… Privacy regulation
ACC Docket
This Week in Privacy: Finding the Best Privacy Control Framework (Sept. 2017).
Articles
Operationalizing the California Consumer Privacy Act (United States) (June 2019).
Sample Forms, Policies, and Contracts
ACC US States’ Privacy Capability Maturity Model (April 2019).






